Technology
1. Introduction
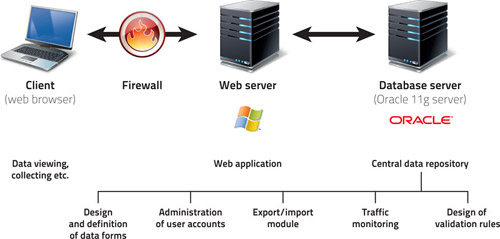
Data security within the registry is of key importance, and a special attention must be paid to this issue. Data of OVARIA project are stored in a database system which was originally based on a modified version of TrialDB system[1-3]. This on-line system has undergone changes in layout and structure, which has made data entry even more comfortable, while security measures have been maintained at the same level as before.
The system has been designed as a robust base for collection of large amount of data in clinical trials and/or clinical registries, is fully customized to the structure of OVARIA project. The on-line application is accessible to users via the internet browser. The security of individual records within the registry is guaranteed via de-identified data collection. Each patient's identity is replaced with a number (ID) which does not allow any backward identification of that person. The unequivocal identification of patient is only known to the attending physician or to an authorized health care professional.
The main advantages of this system involve centralized administration, uniform appearance of forms for data collection in all registries and easy development of new, extending functions.
2. Basic characteristics of the system
- The system is very user-friendly: all data are entered via web forms which are analogical to paper collection (classical CRF).
- The data can be entered into the registry from any computer connected to internet and equipped with the browser MS Internet Explorer 5.5 or higher (it must support the encrypted communication with a 128-bit SSL protocol).
- No additional software needs to be installed on the client's computer.
- Only authorized persons have access to the registry, using their login and password.
- Data in the registry are de-identified, i.e. the patients' records are kept under codes (ID) which exclude any chance that the person might be identified. In this way, the system meets all valid rules on the protection of personal data.
- All data transfer is encrypted in order to prevent a potential abuse during the transfer.
- All submitted data are collected in a central computer - server, where they are safely stored in a database (administered in the ORACLE 9i system).
- Data can be exported for authorized users as a local database for further processing.
- Users can print the filled forms or save them in a local computer in the MS Excel format.
3. Data security
Authorized users can only access the system after entering a valid username and password. The system of user rights is one of key functions in the administration of user accounts. Users can be assigned various levels of authorization so that they have access to selected functions or parts of the system. Apart from this, an automatic log-out is done after a predefined period of user's inactivity. This function is aimed to prevent a misuse of an unoccupied computer if the user forgets to log out.
An encryption protocol is used for data transfer between the user and central database to prevent tapping the communication between the client and server (for example, tapping user login and password). For this reason, any communication between the client and server is realized via the secure protocol HTTPS, using the SSL (Secure Socket Layer) encryption.
In order to provide a maximum data security, other security measures are taken by the provider (IBA), involving mainly the security of provider’s network and the server itself. These measures include firewalls (separating both database and application servers from internet), regular monitoring of the system, monitoring changes in configuration, physical protection of the server room etc.
Additional measures have been taken to prevent potential data loss or damage in case of unexpected events, which are not directly related to information technology. These measures involve fire-stop system, air-conditioned server rooms etc.
Both system configuration and data stored within it are subject to a regular backup. Therefore, even in case of system breakdown, the entire system including the data can be promptly restored.
4. References
- Nadkarni PM, Brandt C, Frawley S, Sayward FG, Einbinder R, Zelterman D, Schacter L, Miller PL. 1998. Managing attribute--value clinical trials data using the ACT/DB client-server database system. J Am Med Inform Assoc 5(2):139-151.
- Nadkarni PM, Brandt CM, Marenco L. 2000. WebEAV: automatic metadata-driven generation of web interfaces to entity-attribute-value databases. J Am Med Inform Assoc 7(4):343-356.
- Nadkarni PM, Marenco L. 2001. Easing the transition between attribute-value databases and conventional databases for scientific data. Proc AMIA Symp:483-487.